What are DDoS Attacks and Why are They so Popular During Cyberwars?

Imagine 100 individuals rushing to squeeze through a gate that can only fit two people, or 1000 cars trying to take the exact same highway exit, at the same moment. Inevitably, the bottleneck will lead to a traffic jam, and then to a complete halt due to congestion.
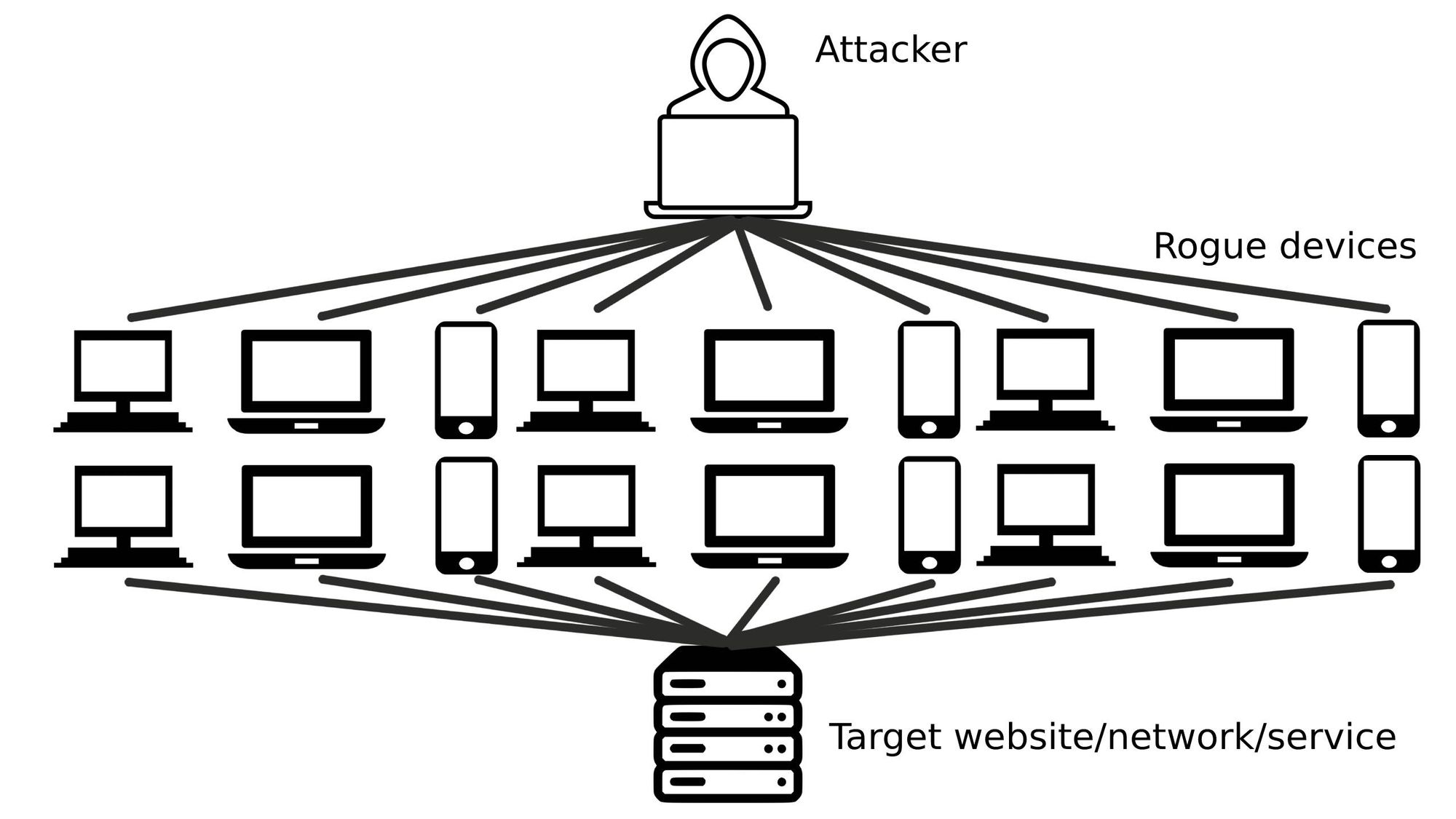
The same principle can be used to explain how a Distributed Denial of Service or DDoS attack works. An Internet-connected computer is artificially fed more commands, requests, and traffic than it can normally handle, which makes it temporarily unavailable to other people and computers trying to make legitimate contact.
Attacks may focus on different areas of the network, and the data volume may vary, but the goal is ultimately the same: to block access to a digital resource. And because everything is run by computers, that means DDoS attacks can take down anything from your gaming PC to websites, payment platforms, mobile apps, and even entire companies.
Why are DDoS attacks so popular?
Unlike other types of cyberattacks, a DDoS attack doesn’t steal information and doesn’t “infect” computers, it just temporarily blocks access by overloading the network while making a powerful statement: “You’re vulnerable”.
Also contrasting other types of cyberattacks, due to its simplicity, the fact that it’s been around for more than 30 years, and the convenience of using automated botnets – thousands of infected computers generating automated traffic, a DDoS attack can be launched by almost anyone, even by people with low tech skills or by groups simply renting the DDoS service.
Why are DDoS attacks used in cyberwars?
The Russian military invasion of Ukraine was preceded by an intense wave of cyberattacks on Ukrainian public institutions and media outlets. These included data-wiping attacks and DDoS attacks and were meant to stir chaos and shatter morale.
In the coming weeks, as both sides resourced to hacktivism groups, DDoS attacks spilled over the border with Anonymous claiming to have shut down thousands of Russian websites, and Russian affiliated groups similarly targeting popular websites in countries that pledged to help Ukraine.
Why are DDoS attacks dangerous?
While DDoS attacks are unpleasant, most of the time the damage they inflict is minimum and normal services are restored in a matter of hours. Other times, especially if they’re targeted at public services like banks, payment services, hospitals, fiscal authorities, or transport companies, they can have more serious consequences,
However, the biggest problem with DDoS attacks is that hackers often use them as decoys and smokescreens to mask much more serious cyberattacks. While everybody is busy mitigating the DDoS attacks, the criminals are silently using other attack vectors to do harm.
What can you do to protect against DDoS attacks?
Unless you’re a gamer, in which case you’re probably already familiar with DDoS attacks and “flooding”, the chances of being targeted by a hacktivist group, as a home user are slim.
Nevertheless, the bigger risk here is that your devices get infected with malware, are enlisted in botnets, and are used to attack other targets. To prevent that from happening you should:
- Watch out for suspicious links and attachments received via e-mails or messenger
- Regularly update your devices with the latest security updates, this includes your IoT devices, not only your computer and phone
- Install a complete security solution that protects your devices from malware so you can focus more on the things that matter
- Consider running a VPN to hide your IP, protect your privacy and secure your data transfers
tags
Author

Radu is a tech-geek with 15 years of experience in writing, journalism and copywriting. When he’s not writing he’s probably taking something apart, trying to figure out how things work.
View all postsRight now Top posts
Start Cyber Resilience and Don’t Be an April Fool This Spring and Beyond
April 01, 2024
Spam trends of the week: Cybercrooks phish for QuickBooks, American Express and banking accounts
November 28, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








